“Should I use passkeys?” my friend asked recently. Like many, they were curious about this emerging technology that promises to replace traditional passwords. “Probably,” I responded, but I realized I couldn’t articulate exactly why. While I knew passkeys leveraged public key cryptography to enhance security, the details were fuzzy. I promised to research the topic thoroughly and report back. Here’s what I learned:
What are passkeys?
Think of passkeys as a smarter, more secure way to prove you’re really you online - without having to remember any passwords. They work like a digital version of your house keys, but better. When you set up a passkey, two special digital keys are created: one stays safely stored on your device (like your phone or laptop), while the other lives with the website or app you’re using. These keys work together like a sophisticated handshake that happens automatically whenever you want to log in.
Instead of typing “monkey123” or trying to remember if you used an exclamation point or the number 1 in your password, you simply prove it’s you by using something you already do or have - like your fingerprint scan, face recognition, or device PIN. Your device then handles all the complex security stuff behind the scenes.
The FIDO Alliance officially defines a passkey as:
A passkey is a FIDO authentication credential based on FIDO standards, that allows a user to sign in to apps and websites with the same process that they use to unlock their device (biometrics, PIN, or pattern).
How do passkeys work?
Let’s try a medieval story to describe the basics of passkeys. If you prefer, you can skip past to the Kayak example below.
Imagine medieval Europe's sprawling network of castles and kingdoms, where the difference between a genuine royal command and a clever forgery could mean life or death. At the heart of this system lay an ingenious innovation: the royal signet ring and its public counterpart.
Every king possessed two critical tools: their private signet ring - a masterpiece of goldsmithing with intricate designs unique to their lineage - and public seal molds distributed throughout their realm. These public molds were like the king's signature made physical, placed in every noble court and major township.
Picture a critical moment: A messenger arrives at a fortified castle on a stormy night, claiming to carry orders to access the royal treasury. The castle's steward, wise to the ways of deception, knows that appearances can be deceiving. But they also know the elegant security of the royal sealing system.
The messenger presents a parchment sealed with deep red wax, impressed by what they claim is the king's private ring. The steward retrieves their public seal mold - a negative impression that should perfectly match any genuine royal seal. Like a key fitting a lock, a true royal seal will align perfectly with every groove and pattern of the public mold.
With careful precision, the steward compares the wax seal to their mold. This is where the brilliance of the system shines: while any forger might know what a royal seal looks like, only the king's private ring could create an impression that perfectly matches the public mold in every minute detail. Each spiral, each heraldic beast, each tiny imperfection must align exactly.
This system's genius lies in its one-way nature: while anyone can verify a seal's authenticity using the public mold, only possession of the private ring - kept under constant guard in the king's personal chambers - allows the creation of authentic seals. Just as in modern cryptography, the public key (the mold) can verify but never create a valid signature.
An Example using Kayak
Creating Your Account: A Modern Take on Authentication
Let’s walk through the account creation process:
- First, provide an email address to begin establishing identity.
- Instead of asking for a traditional password, the website prompts to create a passkey.
- A password manager (in this case, 1Password) steps in to handle the technical details of generating and storing the keys.
Logging In with Your Passkey
Start with clicking “Sign In”:
- Kayak sends a unique cryptographic challenge to the browser, essentially asking “Prove you’re really you.”
- The browser recognizes this as a passkey request and seamlessly hands it off to 1Password, where its private key is securely stored.
- Before 1Password can use the private key, it needs the user’s permission - what’s known as a “gesture.” This extra security step can be completed in one of two ways:
- Biometric verification (like a face or fingerprint)
- Manual verification (a vault password or PIN)
- Once the user has verified their identity, 1Password uses the private key to sign the challenge, creating a unique response that proves the user is the rightful account owner.
Cross-Device Authentication: Using Passkeys on Public Devices
- When attempting to log in to Kayak from a browser without 1Password installed, instead of seeing the usual “Use Passkey” dialog, the user is presented with a QR code.
- Scan this code with the user’s mobile device, which already has both 1Password and your Kayak passkey stored.
- The QR code reaches out to Kayak initiating the passkey authentication process.
- The phone triggers Face ID to unlock and use the passkey’s private key and return a signed message back to Kayak authorizing the user for access.
-
The browser on the public device automatically redirects to the user’s logged-in homepage.
- This approach offers both convenience and security: one can access their accounts from any device while keeping their passkey safely stored on a trusted mobile device. It’s a perfect example of how modern authentication can be both more secure and more user-friendly than traditional passwords.
The QR code that pop from a browser that doesn’t have access to a passkey
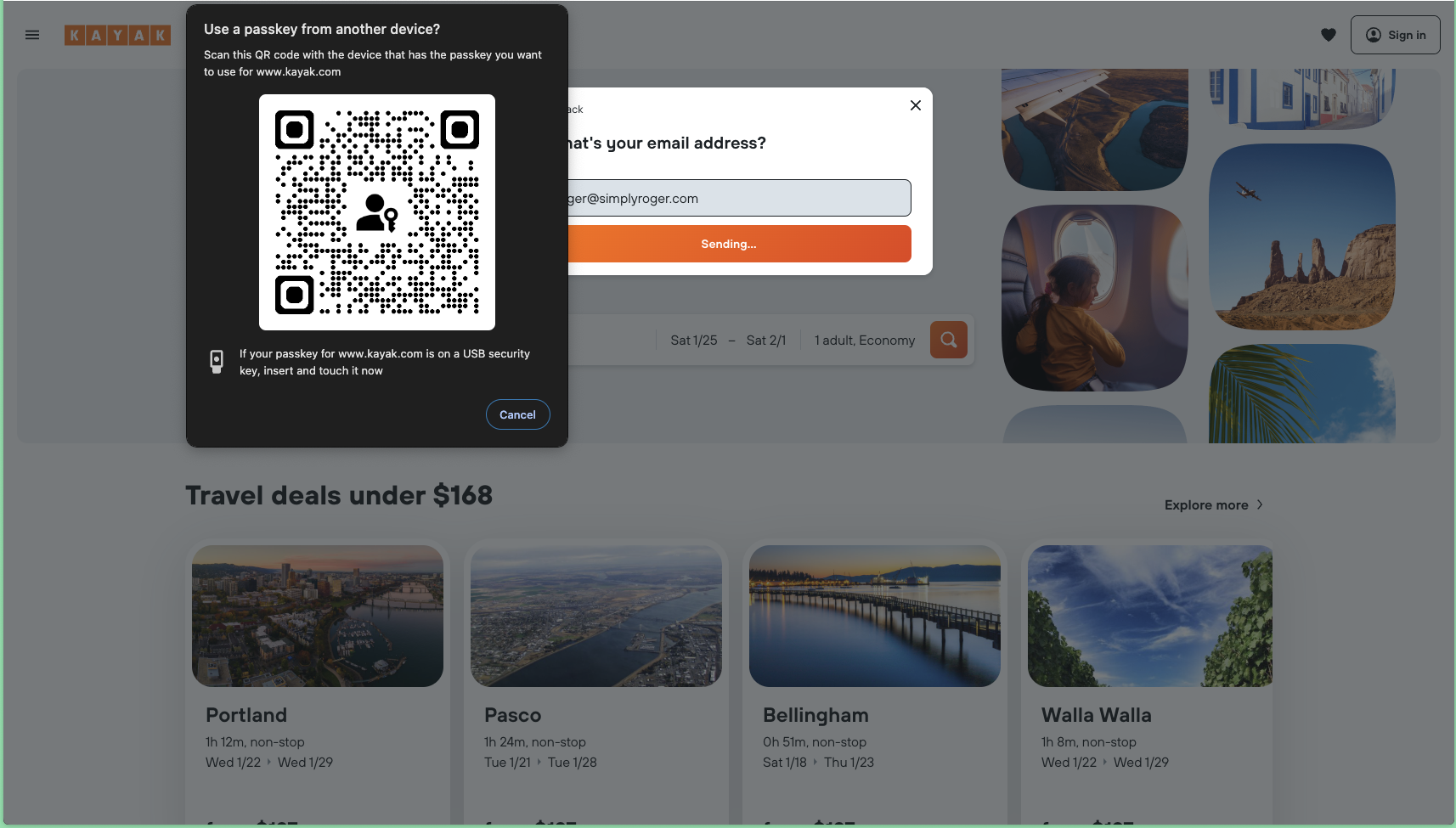
The scanning and authenticating from a mobile device:
Are passkeys better than passwords?
The beauty of passkeys is that they’re both more secure and easier to use than passwords:
- You can’t forget them (they’re stored securely on your device)
- They can’t be stolen in a data breach (each passkey only works with one specific service)
- They’re practically impossible to hack (thanks to sophisticated encryption)
- They protect you from phishing (they only work with legitimate websites)
Passkey Concerns?
The Hidden Security Risk: Legacy Passwords After Passkey Setup
Think of an online account like a house with two doors: a modern, high-security smart lock (passkey) and an old-fashioned lock with a key under the doormat (password). No matter how sophisticated the smart lock is, a thief can still get in through the old door.
When a passkey is set up, many services keep the original password login active by default. This creates a critical vulnerability - attackers don’t need to break the passkey’s advanced security; they can simply target the weaker password option. It’s like installing a state-of-the-art security system while leaving a ground floor window unlocked.
To truly secure the account:
- After confirming the new passkey works reliably, disable password-based login if the service allows it
- If password login can’t be disabled, use the passkey exclusively to build a secure habit
- Consider choosing services that offer “passkey-only” authentication
Remember: Your account’s security is like a boat - it doesn’t matter how well you patch most of the holes if even one remains. A single password vulnerability can compromise all the advanced protection that passkeys provide.
Passkey Loss: Understanding the Risks of Digital Lock-Out
Unlike passwords which can be reset through email verification, passkeys operate on a fundamentally different principle - once lost, they’re gone forever. Think of it like losing the master key to a high-security building: there’s no locksmith who can make a copy. The good news is that modern cloud services provide robust backup solutions:
- Apple users can secure their passkeys through iCloud Keychain
- Google Account holders can sync across their Android devices and Chrome
- Password managers like 1Password and Bitwarden offer encrypted passkey storage
However, if you choose to store passkeys locally on a single device, you’re walking a tightrope without a safety net. A lost, stolen, or damaged device means permanently losing access to your accounts. In such cases, one will need to go through each service’s account recovery process and create new passkeys from scratch.
Best Practice: Always ensure passkeys are backed up to a trusted cloud service or password manager. Just as one wouldn’t keep the only copy of a house key in their pocket, don’t risk storing passkeys solely on one device.
Technical Details
Let’s break down how they work.
A passkey is essentially a pair of cryptographic keys that work together to prove identity - similar to having a lock and a unique key that opens it. The system uses two components:
- Public Key
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDsI3MXKDBV4NLXgNE1+VHujR+f0JQLCxt/HXY5m3cfLBEUezI3XZfMwgdeRzscKFKjejc8dwiMBX7ya+BcVOxohr0K4/tPJ2UCvD4PxfI5KO+fcmqYpeE6/upwtQgThptTwdm6JBWxT6TvUucS6PB1em95B5gxVutu9d1Boeoc0rqIqiKn7AaAcj+Po7l5lRTQtW1MF26aeyM25N+VxPuTrwnECOq28nCtpXJPMi/GQzRqrebqWTHNJg6zsSDFJF4zk1XyqnDJg1ilxTX7jIxyd08btFpmadoTE/E5CAPUaf3Yf+Wqj/19RAbSdhTyHUek5EQBvBmxOqYIfyicZOMkv8fZz++8gbgTxT5LzlY7Y+8e+pScaSuGckZ2oa3RyXWHgENZzhupYwLEB/aHaFl8Izj+yqbk8E7T7hakiyj+mDyvuoyq3b8XEUxJ8tQm6MRLbbMJ0KUOkdcddK1u10nwYxZj/OkGNtf9Y4F25s3HDu51JTYHHnmHhTCw9K+AWZc=Think of the public key as a digital address - it’s completely safe to share with anyone. When one registers with a website or service, the site stores this public key, much like how a post office keeps your mailing address.
- Private Key
-----BEGIN OPENSSH PRIVATE KEY----- [... key content omitted for brevity ...] -----END OPENSSH PRIVATE KEY-----The private key is a secret proof of identity. It never leaves the user’s device and is securely stored in the device’s secure enclave or other key vault, protected by biometric authentication (like Face ID or fingerprint) or your device passcode. This is similar to how you wouldn’t share your house key with anyone.
Understanding Digital Signatures in Public Key Cryptography
Digital signatures are a fundamental application of public key cryptography that ensure authenticity and non-repudiation of messages. Let me explain how they work with a real-world example.
A digital signature is like a tamper-evident seal on a digital message. It provides two crucial security properties:
- Authentication: Proves who sent the message
- Integrity: Proves the message hasn’t been altered
How It Works: A Real-World Example
Let’s say Roger wants to send secure messages to Daniel. Here’s how they would use digital signatures:
Initial Setup
- Roger generates his key pair (public and private keys)
- Roger securely shares his public key with Daniel
- Roger keeps his private key secret and secure
Sending a Signed Message
When Roger wants to send a message to Daniel:
- Roger writes his message: “Transfer $100 to Daniel’s account”
- Roger’s device creates a digital signature using his private key
- The message and signature are sent to Daniel
Verification Process
When Daniel receives the message:
Daniel’s device uses Roger’s public key to verify the signature If verified, Daniel knows:
- The message definitely came from Roger
- The message hasn’t been tampered with
Attack Scenario
Let’s see what happens when a malicious actor tries to impersonate Roger
- The attacker (BadActor) creates a fraudulent message: “Send $1000 to account X”
- BadActor can’t sign it with Roger’s private key (they don’t have access to it)
-
Even if they sign it with their own private key:
- The signature won’t verify with Roger’s public key
- Daniel’s device automatically rejects the message
- No manual verification needed
Real-World Applications Digital signatures are used in many secure systems:
- Code signing for software distribution
- Email security (S/MIME, PGP)
- Document signing (PDFs, contracts)
- Blockchain transactions
- And now, passkeys for web authentication
This same principle of digital signatures is what makes passkeys secure for website authentication. When you log in with a passkey, your device creates a unique signature that proves you possess the private key, without ever revealing the key itself.
References
FIDO Alliance. (2024, November 20). Passkeys. https://fidoalliance.org/passkeys/
Wikimedia Foundation. (2024, December 4). *Public-key cryptography. Wikipedia. https://en.wikipedia.org/wiki/Public-key_cryptography
